
Featured Blog | This community-written post highlights the best of what the game industry has to offer. Read more like it on the Game Developer Blogs or learn how to Submit Your Own Blog Post
Robot Tales: Malicious game clones
What happens when your game earns its own ad-ridden malware clone? We explore the issue on the basis of Robot Gentleman's recent experience with a clone of 60 Seconds!.

Game cloning? Does it have anything to do with Dolly the sheep or stormtroopers? Every game developer who has had the sad opportunity to experience it first-hand knows that is not the case. If and when they decide to provide an account of what they went through, the rest of us can learn what can be done to avoid or at least prepare for such a scenario. Only a few days ago we found out that someone took the liberty of making as part of the "cloned" crowd. Time to share our story.
We released our debut title 60 Seconds! on desktop computers back in 2015. It originally started off as a simple Unity prototype with the intent to test if the engine would be a good fit for us. Almost two years later we had a game that was ready to ship, severe sleep deprivation and spines that resembled a nicely calligraphed letter 'S'. We were hopeful 60 Seconds! would provide enough to keep our studio, Robot Gentleman, going. Its success caught us by surprise. The degree of freedom it gave us was astonishing and terrifying. It took us a few months to figure out how to operate and make sure we do not do anything silly, such as buying a maniac mansion or expanding our team like crazy. After coming back from Indiecade 2015 finals we decided we would love to see 60 Seconds! on more platforms. Player feedback and our own gut feeling pointed towards the same direction: mobile was the way to go.

We decided to approach the project cautiously and start with the iOS version. This move was rationalised by going for a premium sales model and the intention to limit the supported hardware. The happy day came in September 2016 when the game was unleashed on iPad and iPhone users. We were enthusiastic to see the price tag was not discouraging for our audiences and within three months mobile 60 Seconds! was played by over 100 thousand players. This was a great complement to the 300 thousand sales mark on Steam. Crossing that line and feedback from our fans set our eyes on Android.
We were certain that if by this time there were no incidents of cloning our game, we should be fine. 60 Seconds! was too small of a deal to get ripped-off by income-hungry corporate-sized cloners [2], but also too complex to be easily replicated by a tiny team [3]. Vlambeer's experiences with Ninja Fishing [1] seemed like the only scenario that may have been a viable threat to us. What we did not anticipate was that someone had a different idea on how to monetise our success for their own means.
On 13th of January 2017 a malware/adware clone of 60 Seconds! found its way to the Google Play store.
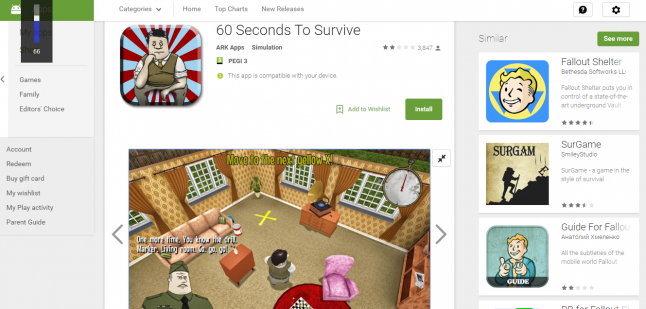
It didn't seem very serious at first. Someone made a simple app with stolen assets from our game and its marketing art. The app would only load what looked like the main menu from 60 Seconds!. Any interaction with it brought up a loading screen, which generated tons of ads. Just before the loading was to be concluded the app crashed. With a lot of folks eagerly waiting for 60 Seconds! to be released on Android, and all the attention other versions of the game received, it was inevitable that downloads would spike soon. The fact that it was made available for free did not help and also made players overlook the fact that the app requested a wide spectrum of access privileges on their devices.
When we found out on the 16th the number of players was still below 5000. Quite a few of the reviewers who downvoted the game did not realise it was not the official version of the game from Robot Gentleman. We were concerned some of our fans may think we are responsible for this atrocity. To counteract we immediately reached out to Google, reporting the incident with their copyright infringement forms and attempted to contact people at Google we've met personally in the past.
As of the 22nd of January we have not heard back from any of them, despite following up on the issue through formal and informal channels. What is worse, the app climbed to 50k - 100k downloads and another, similar malware clone was uploaded to Google Play. Tracing the account that released the first app we found out that a similar strategy was used with three other games before. These clones were either banned by Google or taken down by the "developers" themselves.
This case may not be as bad as some other cloning scenarios. When discussing the Ridiculous Fishing cloning, Rami Ismail from Vlambeer [1] claimed that they have lost a million dollars to the team that ripped their game off. Luckily for us, we are not losing potential revenue. Not yet, anyway. However, the damage caused by whoever malwared our game may be very real. We care about our player community, present and future, and we consider this a problem that should not be ignored. Some players believe what they are downloading is the official release of 60 Seconds!. In fact, we only found out about the malware clone, because one of our fans contacted us through Facebook with a request to fix the Android version of the game. We cannot be entirely sure how this situation will develop. It may affect the popularity of our game on Android, should we decide to enter Google Play, as well as impact the game's and studio's reputation.
This problem could have been resolved at the app review stage, but it would seem that Google Play's review process, which supposedly involves human in the procedure [4], did not work. Still, averting the damage was possible in a day or two, if the platform owner was to step in. Unfortunately, the lack of response from Google prevents that. It makes the whole situation frustrating and confounding for us. Instead of acting quick, we have someone benefitting from our work at the expense of our fans and causing potential PR damage to our studio. We do not have any timeframe on when this malicious app will be shut down and the appearance of its second version is a sign this whole mess is far from over.
Is there anything that can be done to end this right now? Not really. We can contact Google via our lawyers to make the copyright infringement report more official, but that does not guarantee anything and will take time. With more people getting tricked by the malware clone, more ad revenue is generated. In the age of post-truth and the discoverability crisis on game distribution platforms, it is not hard to imagine scenarios like that happening more and more often and affecting developers both big and small. This has been an ongoing issue, since the entry level for game development and games distribution was lowered in the past few years.
As our example suggests, at this point cloners do not even have to expend any effort to clone an entire game. All they need to do is "impersonate" the game using official artwork, build up a fake profile to lure players into installing the supposed game and they can start reaping the profits. One may consider this phenomenon facade cloning. If platform owners, fans and the actual developer are too slow to respond, cloners can get several days’ worth of ad revenue money, making such a ruse a highly profitable endeavour. All it takes is repeating it over and over again with one or more recognisable titles.
Sharing the experience seems like the best thing we can do, in case you were not aware what may be coming to your games. Be prepared.
Update #1: as of 23/01/2017 the app's downloads are between 100 and 500 thousand and we have still not heard back from Google Play. The cloner is using a strategy of "releasing" new versions of the app to lure back players who assumed the app was not crashing intentionally.
Update #2: Google got back to us in the end and took down the malware app in the evening of 23/01/2017. Another clone is currently available on Google Play and we filed a second report with Google. We can't be exactly sure how much money the clone made with ad spamming, but with hundreads of thousands of installs our guess is that it was much more than the $25 Google Play registration fee. Facade cloning seems like a parasite dream come true.
Update #3: Two more clones available on Google Play as of 24/01/2017. We reported them to Google. Seems like this is a beginning of a neverending clone story. It seems that with every clone, more "features" are available and not as many ads.
[3] http://www.gamasutra.com/view/news/214122/Threes_clones_and_cornflakes_A_view_on_casual_games.php
[6] http://iwantaclone.tumblr.com/.
Read more about:
Featured BlogsAbout the Author(s)
You May Also Like







.jpeg?width=700&auto=webp&quality=80&disable=upscale)








