Trending
Opinion: How will Project 2025 impact game developers?
The Heritage Foundation's manifesto for the possible next administration could do great harm to many, including large portions of the game development community.
Road to the IGF 2022: Midnight Protocol draws the player into the world of hacking, having them collect data and sneak their way into secret archives as they work to figure out why they were doxxed.

This interview is part of our Road to the IGF series.
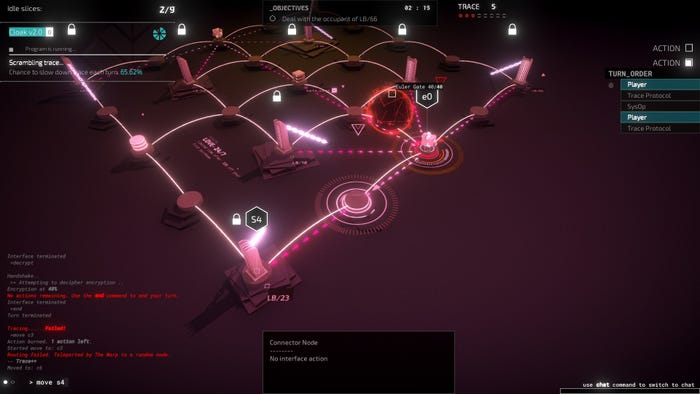
Midnight Protocol draws the player into the world of hacking, having them collect data and sneak their way into secret archives as they work to figure out why they were doxxed. As to how players get there—finding information to use for blackmail, helping agencies track rogue hackers, and more—they'll have many available roads to their goal, depending on the information they manage to pry out using their skills.
Game Developer spoke with Sam Agten of LuGus Studios, the developers of the IGF Excellence in Design-nominated title, to chat about how board games influenced the game's approach to hacking, using keyboard-only controls to immerse the player in the experience, and the challenges that came in creating a visual style that made things clear—while still conveying that feeling of doing complex hacking.
What's your background in making games?
Sam Agten (creator and lead developer of Midnight Protocol): I’ve been making games since college, although nothing that I was ever keen on releasing. I approach game development much in the same way as sketching: Most of the designs end up in the garbage bin. I taught indie game development at a local school on the side, which is how I got a job as a technical artist at LuGus Studios.
At LuGus Studios, I worked on several games such as Liftoff. After a few years, I left LuGus Studios to work on my own project, Midnight Protocol, which conversely got picked up by LuGus and Iceberg Interactive. Life’s curveballs!
How did you come up with the concept for Midnight Protocol?
Agten: I play a lot of board games (they’re great!) and I fell in love with a card game called Android: Netrunner, which is the greatest card game ever made. Netrunner got me thinking about hacking as a mechanism in games and how it is often an afterthought, an overly simple minigame, or they try too hard to be simulationist while still retaining some measurement of approachability. It seemed there was a lot of unexplored design space when it comes to hacking games, both from a mechanical standpoint as well as how immersive they can be.
What development tools were used to build your game?
Agten: Unity, Visual Studio code, Blender and some Photoshop. Awesome tools!
The game very specifically uses keyboard-only controls. Why was this such an important control scheme for the game?
Agten: I think the keyboard-only controls are at the heart of the game. If you’re developing a shooter, you can’t really put a gun in the hands of the player, but when developing a hacking game, the weapon of choice is right there in front of you. What better way to put the player in the shoes of the character?
Besides our greatest source for immersion, the keyboard gives us leeway to take inspiration from the way an actual computer terminal works. If we used a mouse control scheme, a lot of the user actions would be multi-step processes, while typing out a command can communicate user intent very clearly. Finally, it’s a nice throwback to the way old computer games work.
There are downsides, of course. You lose a bit of discoverability and I’m sure a keyboard-only user interface is not for everybody. But gosh darnit, doesn’t it make you feel like a hacker?
What thoughts went into expressing the player's actions through the visuals of the game? How did you decide on the game's visual style, UI, etc? What mood did you want them to evoke?
Agten: Oh man, that’s a difficult question. We looked at a bunch of fictional UIs used in movies and took some inspiration from that. We wanted to stay away from the 80's cyberpunk theme and veer towards a more modern, minimalistic user interface. If you would look at someone playing Midnight Protocol from a distance, we wanted it to look like the player was undertaking a complex task, with a lot of windows, etc. Finally, we stayed true to the classic look of terminals with a sparing use of color.
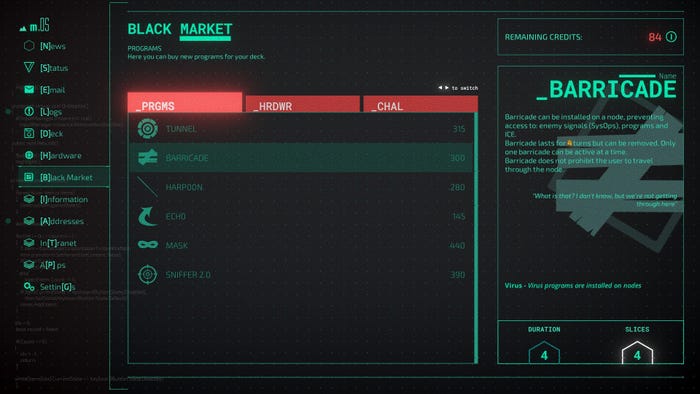
The look of the networks was decided early on. In tools used by programmers, networks are often visualized as a node network. To stay true to its board game inspiration, we made the nodes look like pawns on a board. To make this come across as a digital world, we used a lot of abstract, mathematical shapes. A lot of the programs or ICE that are in the game are also developed by different people with different backgrounds and ideas, so there wasn’t a through line in how we wanted these to look.
Hacking is a highly complex task. What thoughts went into making it more approachable for an audience that likely doesn't know much about the actual processes of hacking? How did you make the complexities of hacking approachable to your average player?
Agten: The intent was never to be realistic about hacking. We wanted a fun game first and a hacking theme second. Narratively, we do use a lot of real-world terminology (phishing, deep faking, etc), but the gameplay is in no way representative of real-life hacking. The way you input your terminal commands, however, is pretty close to how a Linux terminal functions. In fact, you can even use some real world commands instead of the fake ones.
That said, the onboarding was quite challenging. The terminal can be quite scary, and we use some unique mechanics in the game such as the program management and resource system. The tutorial/demo was the part of the game we iterated the most on, for sure. We went to a few conventions (when that was still allowed) to gather a ton of user feedback to help improve that part of the game.
How did you use minimalist visuals to help better convey the complexities of hacking to the player? To make a complex task seem more approachable?
Agten: I think we stayed true to form here and let the command line do the heavy lifting. A lot of the intricacies of the game are communicated through that command line. Getting players to pay attention to what that command line is telling them was a bit more difficult. The sparse use of color and the big, bold, red letters of an error message hopefully help out in that department.
We also wanted a more complex looking UI to serve that hacker fantasy a bit more. Some stuff, like the remaining number of actions you have, for instance, is actually shown multiple times. In this way, we create that visual clutter we are hoping to have without actually dumping more information on the player. Having the same information in multiple places is also something I’m going to take away from this project and bring to whatever comes next because of how much easier it makes for the player to discover information.
What thoughts went into the tools and actions players could take in the game? How did you choose the ways in which players could hack in this world?
Agten: You might tire of me saying it, but I think we borrowed from board game design to make a complex task seem simple. Board games have to do a lot with very little. There’s no processing power except what your players can remember. We wanted to set out the language of the game early one and stick to it.
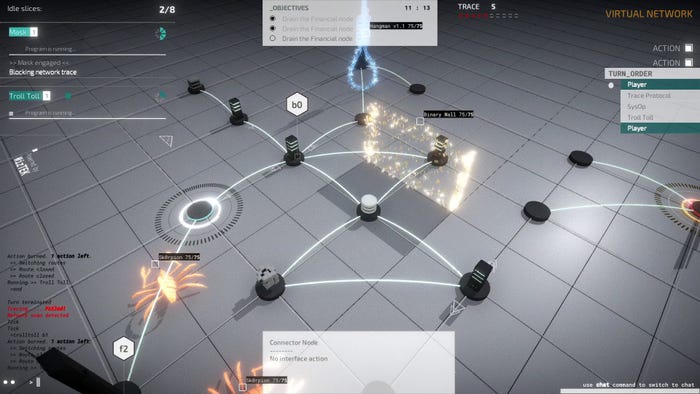
At its core, Midnight Protocol is a familiar formula. You can do 2 things in a turn. You can move, interact with your current space, or use an ability. Everything else just builds on that foundation. A good example of this is the System Node. From a player’s perspective, it functions like every other node: you move to it and burn an action to use its interface action. In the case of a System Node, this opens up a menu of choices.
This means that, from a design perspective, the System Node is a wildcard. Decrypt highly sensitive government data? System Node. Download someone else’s photos from iCloud? System Node. We tried to keep the player’s language simple but with enough affordances to allow for cool objectives. The keyboard control scheme helps too, because even though you are doing fairly simple things as a player, typing them out in a command line helps to make them feel complex. At least, that’s what we were going for.
What research did you do to help flesh out your hacking game? How did this research affect the game you created?
Agten: I actually have another day job as a teacher at a local university. Among other things, I teach a cybersecurity course which helps me get a better understanding of the way real cybersecurity works. We also conferred with a bunch of other cybersecurity specialists, such as penetration testers and bug bounty hunters, to get a feel for how we could introduce some facts into our fiction.
Fun, spoilery fact: the endgame mission revolves around the BGP protocol, the very same, very real protocol that took down Facebook (or should I say Meta?) a few weeks before the game launched.
One of the things I hope we get across in this game is how cybersecurity is a very human thing. Often, security breaches are caused by human error, not faulty computer systems.
Was the final game largely the same as your initial ideas for the title? Why or why not? Why did it change, or why did it stay largely the same?
Agten: I think the core of the game remained roughly the same but it became an infinitely better game thanks to the feedback from colleagues, friends and playtesters.
As a designer, you go looking for the fun in your game and then try to flesh that out a bit more. The resource system, for instance, was one of the very first things I designed, and so was the idea of the trace, stealth programs, and breakers. That’s all in there, albeit in a much more refined form. But I also envisioned the game in real-time and with a pdf manual. Thank goodness for early playtests that showed that that was a stressful experience and not a fun one.
I think the biggest change was the increased focus on narrative and how crazy we could go with the hacking theme instead of just adding more and more complex programs or networks. I’m really proud of how we added a lot of fourth wall breaking secrets and easter eggs to the game, because I think that really fits the hacking theme. Why shouldn’t we have a hacking game where you can mess with your own save game? Why shouldn’t we tuck a mysterious file next to your game files? We want to encourage you to go looking, just like curiosity drives a real hacker. Maybe that’s the most real thing about this game?
This game, an IGF 2022 finalist, is featured as part of the IGF Awards ceremony, taking place at the Game Developers Conference on Wednesday, March 23 (with a simultaneous broadcast on GDC Twitch).
Read more about:
[EDITORIAL] Road to IGF 2022You May Also Like