7 games with interesting hacking mechanics all devs should study
Nearly 20 years past "hack the planet!", the heroic hacker archetype still holds a certain appeal. But how to make it interesting in a game? Devs share their thoughts on 7(ish) games that do it well.

Games have immense capacity to make us feel cool or smart or highly capable — or all three at the same time. And few things can pull that off quite like a great hacking mechanic.
These days hacking is more topical than ever, and for anyone making a game that even flirts with the implications of the growing interconnectedness and networking capabilities of objects and devices all over the world — and the sometimes-questionable security protocols protecting them — it's rife for potential as a video game mechanic.
With that in mind, we reached out to several developers for their help building a list of games with hacking mechanics that every dev should study.
Watch Dogs 2 — an open-world hacker's toolkit
Watch Dogs 2's satire-laden cautionary tale on the dangers of unchecked, unregulated technological progress has hacking woven into its very DNA. Whether it's the InfoSec-rooted storyline or the hacktivist credentials of its lead character and his team, or the remote-controlled contraptions and Internet of Things trickery, this is a game that's as much about the ethics of tech-powered vigilantism as about holding technology corporations accountable for their wanton breaches of customer privacy and the security flaws of their products.

It's little wonder, then, that the player is armed with a plethora of fun hacking tools — in addition to all the usual open-world fare. The player can hack into security cameras around the city, remotely hijack cars (either one or many at a time), drain people's bank accounts, redirect electrical currents to power gates and elevators, and much more. Watch Dogs 2 is a fine example in how to give players a large range of ways to interact with the world while simultaneously nudging them to favor a subset of available options. "Even though a wide selection of firearms and weapons is included," notes Quadrilateral Cowboy and Thirty Flights of Loving developer Brendon Chung, "using them just kinda feels like... the wrong way to play the game?"
"Watch Dogs 2 never explicitly says it," he continues, "but everything about the character personalities, dialogue, and tone of the game steers you away from weapons and toward the way-more-fun gadgets and hacking tools."
TAKEAWAY: If the theme and story allows for it, arming players with a hacker's toolkit of special skills and gadgets can be a delightful, refreshing, and possibility-laden way to escape the dominant modality of 3D action and open-world games.
Hacknet and Uplink — Hollywood-style hacking coolness
HackMud developer Sean Gubelman points to both Uplink and Hacknet for the strong theming of their core hacking mechanics. These are games that make the player a cyber hacker in the way popular culture imagines this to be. They're about Hollywood-style hacking, designed to look and feel like elite code cracking and cybercrime without requiring much — if any — actual hacking knowledge.
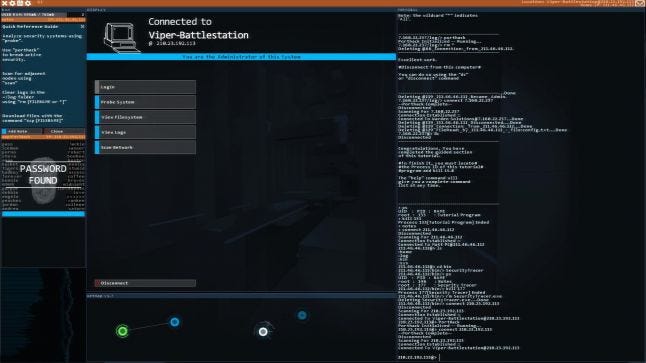
There's an interesting difference in how they do this: in Hacknet, the player spends much of their time typing Unix commands into a terminal interface to break through network security and explore and wreak havoc on the connected systems. Uplink, on the other hand, is more theatrical. It involves building elaborate routing sequences to hide your real IP address, then dialling in and using a password-cracking program to gain access to the target system — with everything depicted in the kinds of fancy, futuristic interfaces of WarGames or the hacking scenes in any number of late-90s movies.
TAKEAWAY: Good game mechanics are never solely about substance. You need the right mechanic in the right place in the right game, and when it comes to emulating highly-difficult real-world tasks like hacking you ideally want another layer: cool. The best hacking mechanics make players feel like they're geniuses, even if just for a moment.
Else Heart.Break() — hacking intertwined with everything
At first glance, Else Heart.Break() seems like a traditional point-and-click adventure game. In truth, however, it's anything but traditional. Its sprawling city is full of places to go and things to do, and its lifeblood is a BASIC-derivative language that makes everything in the city work. If a player clicks on an object with the "hack" command, which is unlocked once the player gets access to a special key, they get to see the object's code — and to change its properties or behaviors. The effectiveness of this hacking mechanic, says Deus Ex: Mankind Divided lead designer Richard Knight, rests on the decision to expose the language to the player — which lends it a "realistic feel" and lets the game become about "solving problems creatively through language expression."
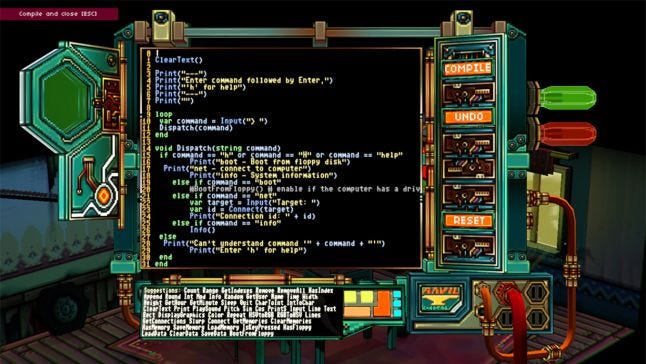
Introversion founder and creative director Chris Delay argues that the critical thing about Else Heart.break() that its hacking mechanic is all-pervasive in its world. "I couldn't believe how far they'd gone with this concept," he explains. "Every door, every item, even food and drink, every system in the game could be analysed and understood by reading its source code, then edited. I found myself wandering around the world just looking for objects to inspect. Eventually, when you find a second key and realise you can now actually hack THE KEY ITSELF, well, my mind was blown."
TAKEAWAY: The best hacking mechanics are often deeply tied to the game's world — they upend rules and logic, reshaping them at least in part to the player's whims.
TIS-100 and Shenzhen I/O — hacking as a programming challenge
Zachtronics' pair of programming games favor the older meaning of computer hacking, from a time when before the term gained its nefarious connotations. They are games about programming for the purposes of mastering a system, solving problems, and experimenting. Knight praises them for the same reasons he recommends Else Heart.Break() — they're about building things (Shenzhen especially) and solving problems in creative ways, using code and simulated circuits.
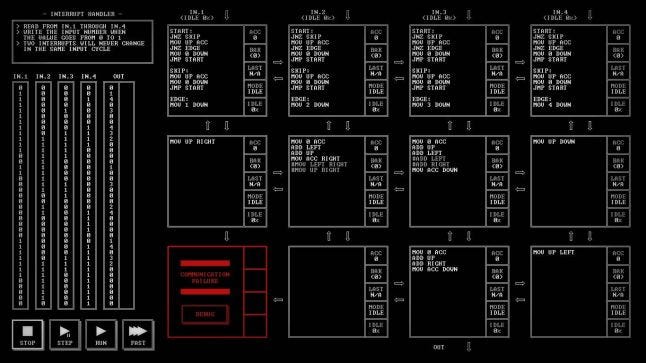
In TIS-100, this means reading a detailed technical reference manual for an imaginary 1980s computer and then manipulating pre-written Assembly code to repair corrupted segments (and then optionally refining this code to minimize its size and required clock cycles, like any self-respecting 1980s hacker). Shenzhen I/O, meanwhile, is more like roleplaying a hardware hacker who's stuck having to make stuff for money when really they're only in it for the challenge of making a radio-controlled LED vape pen or a drinking game scorekeeper that tracks and visualizes past performance. These are games that don't simply have a hacking mechanic; they are simplifications of real-world hacking, as engineers see it — where the entire goal is to solve technical puzzles, for the puzzle, and then to solve them better.
TAKEAWAY: Hacking mechanics, much like real hacking, can be a means to an end or they can be both the means and the end — which is to say that the hacking can be about hacking and not about opening a door or distracting a guard or stealing money or whatever.
HackMud — an exercise in trust
The whole point of HackMud is to behave like a hacker. That means whiling away the hours tethered to the command-line prompt, writing and editing your own scripts and programs and running other people's code when you don't know how or can't be bothered doing something the hard way. Everything except for a few key system commands is player-authored, so there's always a lingering question as to whether it's worth the effort writing a new script or program or worth the risk of using an existing one.
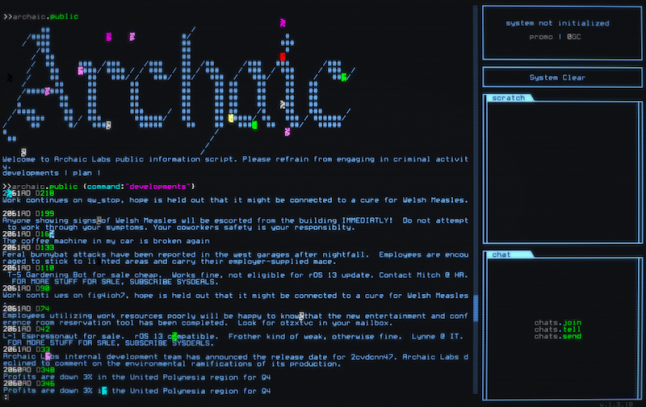
Delay says that he had "a brief obsession" with the game. He praises its treatment of the issue of trust in hacking. "You are constantly trying to ascertain how trustworthy a player or script is, and if they are actually going to steal all your cash (which happens often)," he explains. "There are command line tools to determine how trustworthy a script is, but many of them are written by players as well. The game forces you into a world of hackers and has you fend for yourself. One typo and you can lose everything, especially as most of the 'safe' system commands have nasty malware versions that share the same filename except with a single typo, which your client will happily run if you type the name wrongly."
TAKEAWAY: In the real world, hackers often rely as much on trust and cooperation as on skill and collaboration — so why not make hacking mechanics in games work the same way?
Quadrilateral Cowboy and Gunpoint — hacking as a system
Quadrilateral Cowboy ties its hacking systems into a computer-in-a-briefcase that can be used to control the environment — to switch off lights and open doors or operate lasers and rifles and more for player-specified spans of time ("door4.open(2)", for instance, will open door 4 for 2 seconds). Gubelman says that it does a great job of connecting the world and the typed hacking commands together through puzzles.
.jpg/?width=646&auto=webp&quality=80&disable=upscale)
It's a heist game in which the 3D environment is the puzzle(s) and this simple (but versatile!) hacking mechanic becomes almost like a toolbox. And it's the detail afforded by this combination — the objects in the environment, each placed for narrative or gameplay purposes (or both), but also the precisely-timed sequences of commands and multi-character actions — that makes the game compelling.
Gubelman also points to Gunpoint as a fine example of hacking mechanics that connect a game's world and its puzzles — thanks to a nifty gizmo that allows the player to manipulate the wiring of each level to activate elevators, overload light switches and power pockets, re-wire motion detectors, and so on. As in Quadrilateral Cowboy, these actions don't merely forge a path; they also affect the behavior of other characters and objects. The hacking here is not a parlor trick or an isolated puzzle, but rather a core system that can be played with for sometimes-unexpected environmental consequences.
TAKEAWAY: Even in games with free character movement around an environment, hacking mechanics are more compelling if they work in concert with other systems to produce emergent situations.
Bioshock — hacking abstracted from reality
Knight points out that hacking mechanics need not be in any way realistic. "If it's something far-flung or fantastical," he explains, "a mini-game makes sense as a way to abstract it entirely." In something like the Deus Ex games, for instance, the Internet as we know it has been transformed into something more akin to the worlds of Neal Stephenson's Snow Crash and William Gibson's Neuromancer. Its conception of technology and networking is already abstract, so the "hacking" can be almost anything.
"You could turn it into a turn-based RPG and it would still make sense that you're not port sniffing or running buffer overflows or whatever," says Knight. "Bioshock essentially does the same thing with their clone of Pipe Dream. In both cases, the player is not a hacker. They can hack, but it's a skill to learn for a hero that is usually a clean-slate. A mini-game to master hacking becomes a skill to optimize just as combat and exploration do."
TAKEAWAY: The further a game is from a current day real-world setting, the more freedom you have to make your hacking mechanics unlike real hacking — and you might even be better off making it something completely abstracted away from real hacking.
Press X to hack
Knight also points out that sometimes when hacking is thematically appropriate it need not necessarily be implemented in a game mechanic. "If you're doing something heroic, or rather too easily within the skill of the player, it makes sense not to apply gameplay to hacking at all," he explains.
In Hitman (2016), for instance, the player controls an elite and highly-trained assassin, which Knight suggests makes it perfectly logical that a player to press X to hack a computer or fly a helicopter — he's an expert for whom such acts would be trivial and straightforward. And that then leaves the designers more time to focus on the parts where he is actually at risk — the core part of his job: maintaining cover and assassinating his targets.
Whether it's a plot contrivance, as in this Hitman example, or a core mechanic like in most of the games listed here, or anywhere in between, hacking mechanics executed well can offer both a refreshingly non-violent way to get things done and an intellectual challenge that leaves successful players feeling like geniuses. But take care if/when using them, especially if it's not as a core mechanic, as the line between too complex and too simple may be aggravatingly small.
Thanks to Richard Knight, Sean Gubelman, Chris Delay, and Brendon Chung for their help putting this list together
About the Author(s)
You May Also Like







.jpeg?width=700&auto=webp&quality=80&disable=upscale)








