Capcom ends ransomware investigation, finds culprit gained access via old VPN
Capcom has concluded its investigation into last year's cyber attack and confirmed that no more information has been compromised.

Capcom has concluded its investigation into last year's cyber attack and confirmed that no more information has been compromised.
Back in January, the company said the personal information of 16,415 people had been leaked following the ransomware attack, but has now downwardly revised that figure to 15,649 people.
It also indicated that information relating to roughly 390,000 customers, business partners, and other external parties may have been compromised, and in today's update said there have been "no changes" following that announcement. The Japanese company once again reiterated that "none of the at-risk data contains credit card information."
"At this point in time, the Capcom Group's internal systems are near to completely restored, and while coordinating with the newly established Information Technology Security Oversight Committee, the company will work toward continuously strengthening both security and the protection of personal information going forward," said the company.
"Capcom offers its sincerest apologies for any complications and concerns its customers as well as its many stakeholders may have experienced, and further, would like to express its deepest gratitude for their ongoing support during this time."
The lengthy update includes a pretty detailed breakdown of how the attack played out, revealing the culprit accessed the company's internal network by targeting an older backup VPN device at its North American subsidiary.
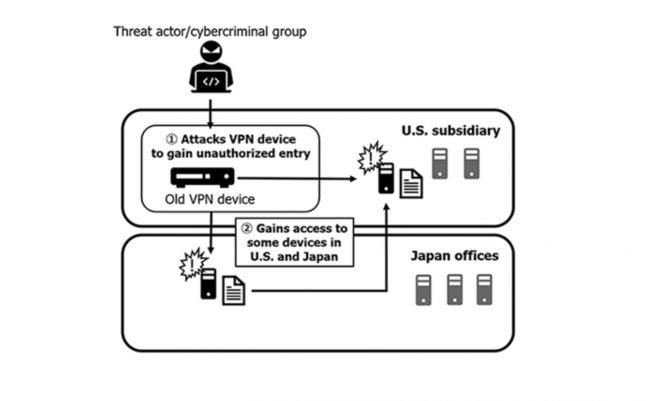
"At that time, the Capcom Group, including the North American subsidiary, had already introduced a different, new model of VPN devices," said Capcom. "However, due to the growing burden on the Company's network stemming from the spread of COVID-19 in the State of California, where this North American subsidiary is located, one of the aforementioned older VPN devices remained solely at this North American subsidiary as an emergency backup in case of communication issues, and it became the target of the attack."
That opening allowed the perpetrator to compromise devices at Capcom's other offices in the U.S. and Japan, infecting them with ransomware that resulted in the encryption of files and the loss of personal information.
The person responsible for the attack also left behind a ransom note instructing Capcom to make contact with a view to negotiating, although it didn't specifically mention a ransom amount. After consulting with law enforcement, however, Capcom chose not to engage with the culprit and "took no steps to make contact."
You can read the full breakdown, including what steps Capcom will take to avoid a repeat scenario and support those affected by the attack, by checking out the full update.
About the Author(s)
You May Also Like







.jpeg?width=700&auto=webp&quality=80&disable=upscale)








